AWS SAP-C02 exam preparation notes
AWS SAP-C02: AWS Certified Solutions Architect Professional (C02 version)
AWS Orgnization
- In AWS Organization, the management account can manage the permission and policy of other accounts, but it cannot directly manage the resources of other accounts;
- Even though by default resources are not shared, there is an option in the Organization to turn on resources sharing. It is essentially AWS Resource Access Manager, which is not technically an Organization feature. Resource Access Manager can share supported resources (such as VPC, subnet) across different accounts or organizations, but normally the invitee needs to accept the invitation. Turning on the Organization resource sharing option eliminates this acceptance step, and also automatically manages the share audience per OU membership;
- For Organization SCP, the evaluation logic is AND. That means, if the root SCP denies a service, even if the OU SCP allows it, OU account cannot access that service.
Security
- Access to CloudHSM is not governed by IAM. It is managed by CloudHSM service itself. CloudTrail has 3 types of events: (1) Management events; (2) Data events; (3) CloudTrail Insights
- KMS multi-region key is a thing. It exists.
- WAF: layer 7 protection (e.g. SQL injection, XSS); AWS Shield: DDoS protection; VPC NALC: Layer 4 firewall
- AWS Firewall Manager: manage AWS Shield, WAF of multiple AWS accounts at one place
- AWS Security Hub: manage security alerts, compliance status of multple accounts at one place
- Amazon Inspector: SAST for EC2 Instance, ECR, Lambda Function
Route53
Records Type
| Route 53 Record Type | Use Case | Failover Capability | Remark |
|---|---|---|---|
| Simple | Map a domain to a single resource (basic DNS record). | No | |
| Weighted | Distribute traffic across multiple resources in defined percentages. | No | |
| Multi-Value Answer | Return multiple healthy records (basic load balancing). | Yes | |
| Latency | Direct clients to the AWS region with the lowest latency. | Yes | Active-Active |
| Failover | Provide active-passive failover between primary and secondary resources. | Yes | Active-Passive |
| Geolocation | Route traffic based on the geographic location of the requester. | No | |
| Geoproximity | Route traffic based on geographic location, with bias control. | No |
Other notes
- Inbound resolver is for on-premise DNS server to forward DNS queries to AWS, and outbound resolver is for AWS to forward DNS queries to on-premise DNS server;
CloudFront v.s. Global Accelerator
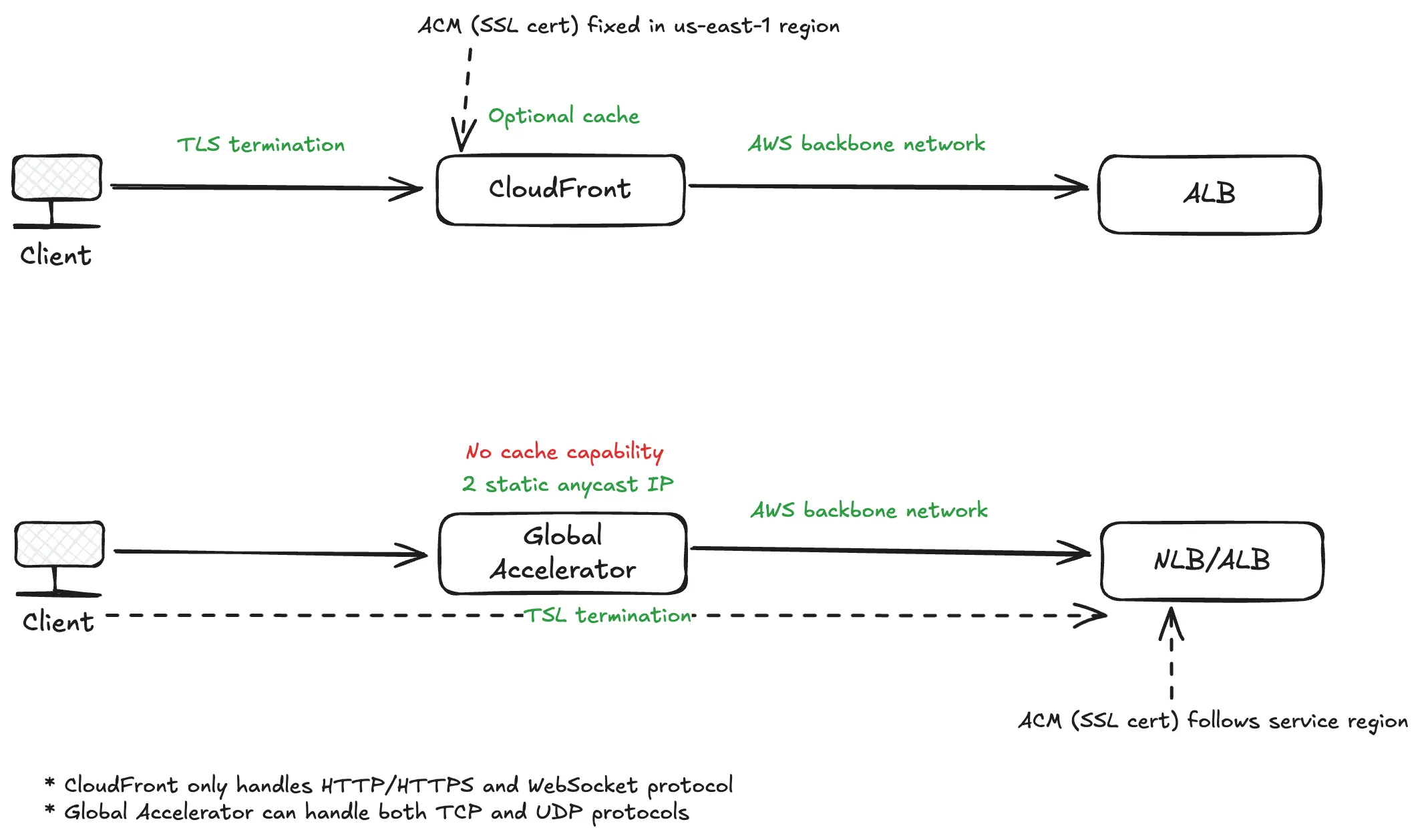
Summary:
- Both CloudFront and Global Accelerator leverages the AWS backbone network, so it speeds up your request;
- CloudFront does SSL termination at the edge, so we must create SSL certificates at
us-east-1region (the only ACM region for CloudFront), whereas Global Accelerator sends request to your service, so you create SSL certificates according to your service region for Global Accelerator; - CloudFront only supports HTTP/HTTPS and WebSocket protocols, whereas Global Accelerator supports more general TCP and UDP protocols.
Additional notes:
- Lambda@Edge is Lambda function running at edge locations. It is similar to CloudFront and its SSL termination happens at the edge location.
Advanced Networking
On-premise & AWS networking
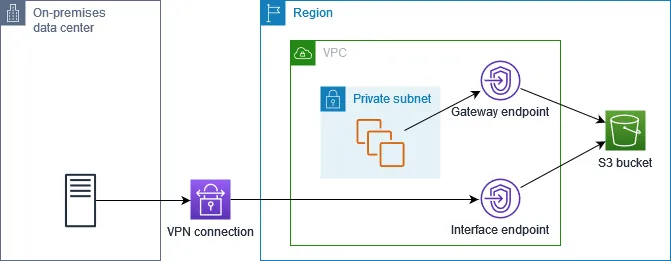
(Source: Gateway endpoints for Amazon S3 - AWS Documentation )
❌ This won’t work: On-premise Data Center -> DirectConnect -> VPC Gateway Endpoint over Private VIF -> -> S3 ✅ This works: On-premise Data Center -> DirectConnect -> VPC Interace Endpoint over Private VIF -> S3 ✅ This also works: On-premise Data Center -> DirectConnect using Public VIF -> S3
The first option does not work because “Endpoint connections cannot be extended out of a VPC. Resources on the other side of a VPN connection, VPC peering connection, transit gateway, or Direct Connect connection in your VPC cannot use a gateway endpoint to communicate with Amazon S3.” (AWS Documentation )
From 2021, AWS introduced PrivateLink. Given that, VPC Endpoint Gateway becomes the option to connect on-premise data center to S3 over private network via VPC Interface Endpoint (AWS Documentation ).
PrivateLink
In addition to on-premise to cloud connectivity, PrivateLink can also be used on the cloud. AWS Marketplace uses PrivateLink to distribute SaaS service.
Comparing with the VPC Peering connection, PrivateLink is more advantageous in this case because the customer can choose their VPC CIDR freely without considering the CIDR clash or overlap to the provider’s, and there is no need to manage route table.
Storage Gateway
- AWS Storage Gateway consists of a series of types, including volume gateway, file gateway, tape gateway;
- By default, data via those storage gateway traverses through the internet. The data is encrypted in transit;
- To ensure the data not to go through the internet, DirectConnect and PrivateLink is usually required.
VPC Endpoint
- VPC Endpoints consist of two types: gateway type and interface type;
- Gateway type of VPC Endpoint is used for S3 and DynamoDB;
- This is different from Storage Gateway. VPC Endpoint routes the traffic through AWS internal network.
REST API vs HTTP API
| Feature / Capability | REST API | HTTP API |
|---|---|---|
| Age | Older, full-featured | Newer, lightweight |
| Price | Higher | Lower |
| Performance | Slower | Faster |
| Request/Response Transform (VTL) | Yes (full VTL) | No (only minimal mapping) |
| AWS Service Integration | Yes (DynamoDB, SQS, SNS, etc.) | No |
| Lambda Integration | Yes | Yes |
| HTTP Backend Integration | Yes | Yes |
| Auth Options | IAM, Cognito, Custom Lambda, API Keys | IAM, JWT (Cognito/OIDC), Lambda Auth |
| Usage Plans / API Keys | Yes | No |
| Advanced Features | Validation, models, caching, etc. | Minimal |
Trivia
- There is no vCPU setting in Lambda. More memory means better computational power. If we need better CPU, we need to increase the RAM;
- ELB (Elastic Load Balancer) is an overarching terminology for ALB (Application), NLB (Network), CLB (Classic) and GLB (Gateway);
- Elastic IP cannot be attached to ALB, but can be attached to NLB.